How good are you at spotting something phishy going on?
Well, before you take this 30-second quiz to put your trigger-happy fingers and thumbs to the test, let’s start with an introduction to what Phishing is, and why you - and your team - need to avoid taking the bait at all costs. And what other place can you learn all about it other than your trusted cyber security service provider?
What is phishing?
Put simply Phishing is the cyber equivalent of spending a leisurely afternoon trying to catch your dinner. Only, it’s done by deceitful IT geeks trying to lure you in with a well-crafted email to catch your confidential details instead.
Since 2003, Phishing has become an increasingly serious threat to individuals and businesses. And that’s because the ‘phisher-men’ (and women) are getting seriously good at the art of deception. Tempting you to click on, what you think is, a genuine email and encourage you to update your confidential details, so they can steal – or encrypt - your information.
In the past, you could spot a phishing email a mile away. Badly composed sentences, spelling errors and the promise to be reimbursed upwards of $10,000 by a prince stranded at the international space station were big giveaways. But today, a phishing email can be difficult to spot, even for the technically proficient.
Take this 30-second Phishing quiz for example. Can you spot what’s real and what’s fake? Fill out the form and give it a go. Oh, and drop your score into the comments, I'd be interested to hear how you go.
How to spot a phishing email
Phishing is a simple – and super effective form of cyber-attack. One peek at the ACCC’s live scam statistics shows as much. The reason for its effectiveness? Because it’s not trying to exploit a technical glitch, instead, it exploits your most vulnerable asset… You.
After all, why waste the time and effort in breaking through several layers of your digital security when they can just mislead you into handing over the key?
Sure, there are some technical smarts we can put in place to help you recover from clicking the wrong email. And you’ll see more of them below.
But with human error leading the statistic for data breaches, you must learn how to spot the difference between a genuine email and a deceitful one, so you don’t give away the keys of the castle to the devious rascal. Take a look at this example below:
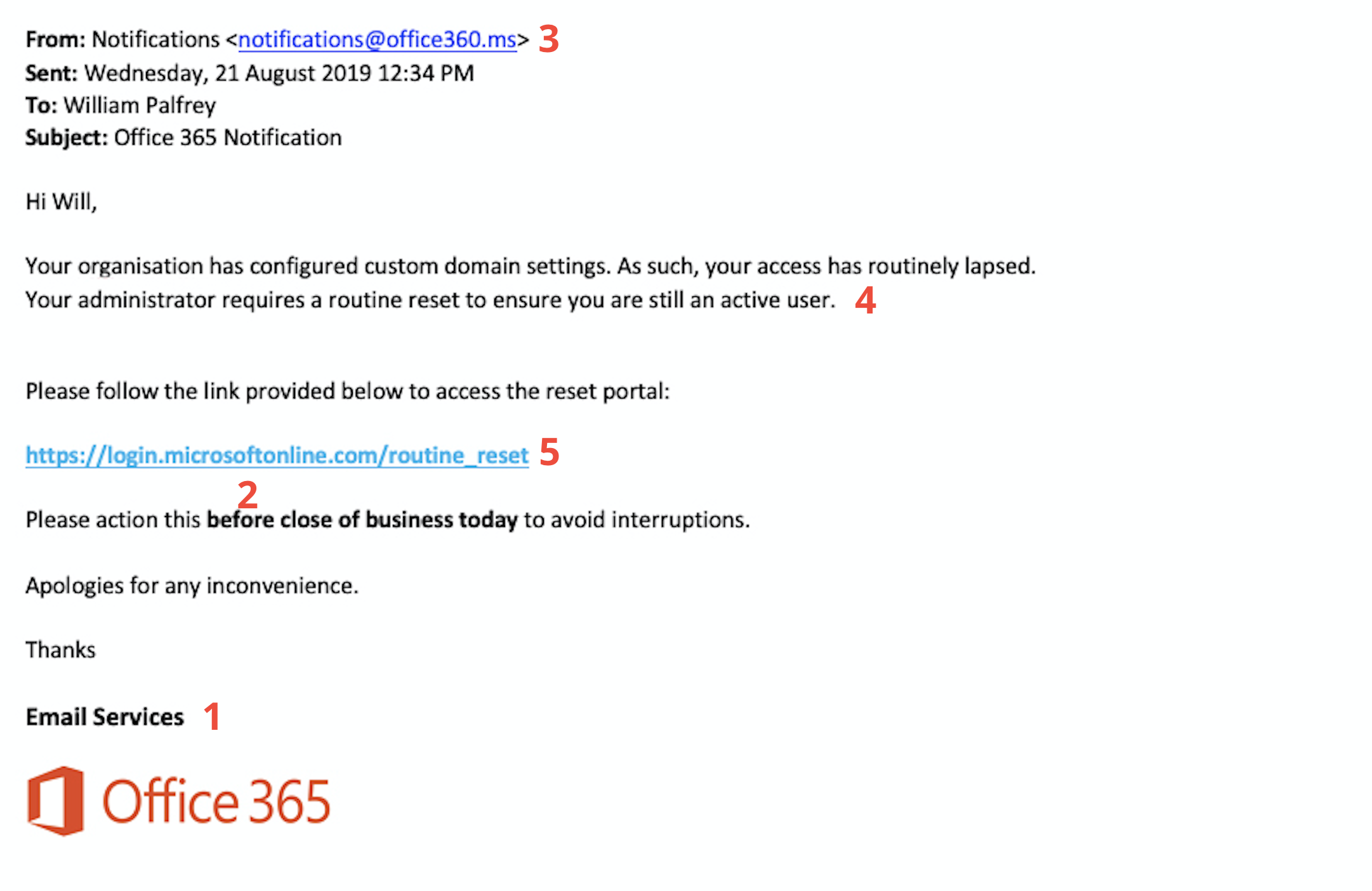
- Before considering anything else, are you expecting to hear from the organisation? If not, it’s a good idea to be overly cautious. And if you’re in doubt, just hit delete. It’s unlikely you’ll end up in as much trouble for deleting a genuine email as you would for opening the wrong one.
- Typically, the copy will portray a sense of urgency and encourage you to take immediate action.
- Inspect the email addresses and domains for inconsistencies
- Is the request something you’d typically expect from the person or organisation?
- Hover your mouse over the links to view the URL destination, does it appear genuine?
As nice as it might be to have a list of Phishing tips to look out for, it’s not guaranteed that every Phishing email will have one of these giveaway signs. Some Phishing emails are almost perfect imitations that don’t show any signs of their deceitful intent, so what then?
Always use your link: Always
If you receive an email that encourages you to update your information or log into your account do not click on the links provided in the email.
Instead, open a new browser window and navigate to the website directly. If the request you received in the email is legitimate, you’ll be prompted with the same request upon logging into the genuine site. Using your link is the only way to guarantee that you’ll be accessing a legitimate site.
Protect your data and your team
The best way to protect your data from Phishing attempts is to stay up to date with current threats, be overly cautious online and ask your IT provider to help you with the technical smarts that can:
- limit the damage a data breach will cause; and
- block malicious messages from reaching you in the first place.
Here are some examples:
Secure DNS
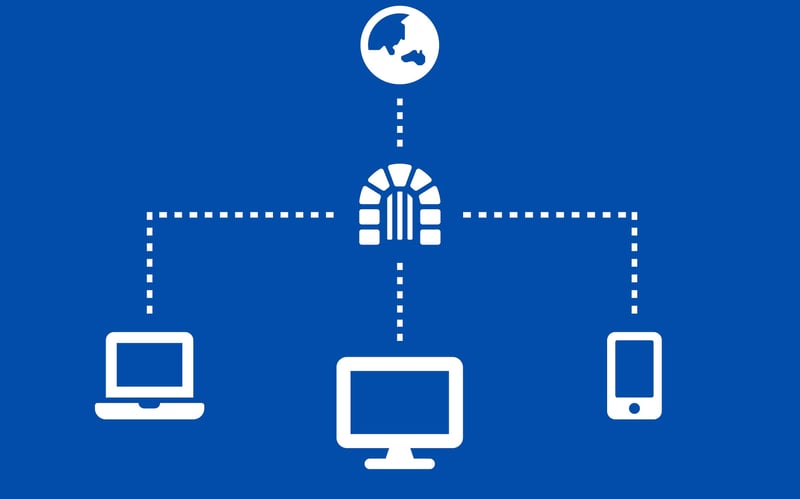
Think of a secure gateway that sits between your team and their interactions with the web. A Secure DNS will help to block your team from visiting insecure, suspicious or malicious websites, even if they click the wrong link.
Anti-Spam
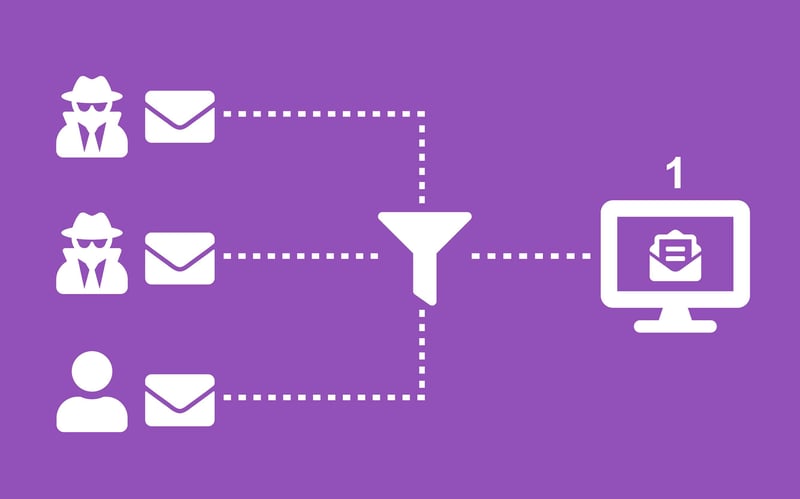
Essentially, it is a filter for your emails. An Anti-Spam service will direct your incoming email through an intelligent filter that strips out the malicious content before it reaches your inbox.
Offsite Cloud Backups
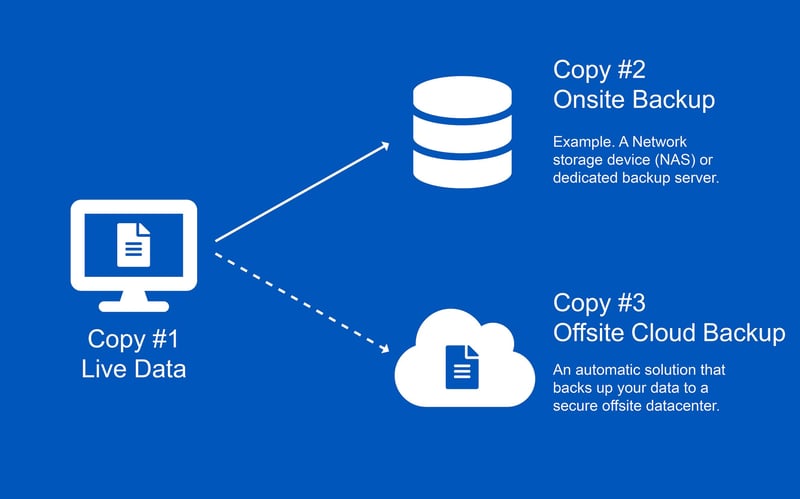
Admittedly, backing up your data doesn’t protect you from Phishing attacks. But it will help you recover from one if your data is encrypted because your credentials have been compromised due to a Phishing attack. And it can happen. Take a look.
There’s no questioning the importance of backing up your data. But it is worth questioning if your backup is working and up to date. Oh, and whether you’re backing up everything you need, to recover from a cyber-attack? It doesn’t take long in fact, you can even copy the email template in this article and send it to your IT team, so you can get all the answers and protection you need.
Password Managers

If your login credentials are compromised by a Phishing attack, cyber-criminals will attempt to stuff your credentials into several online platforms in the hope that you’re using the same passwords for your accounts (Which you’re definitely not doing, right…?).
We know that using a unique and complex password for every single account is easier said than done, which is why we encourage you to use a password manager that takes care of creating – and remembering – unique passwords for you, so you don’t have to.
What to do if you think you’ve handed over your confidential information
If you think your data has been breached or you’ve entered your financial information into a phishing site:
- Contact your financial institution immediately to cancel your cards and/or lock down your accounts.
- Change and update your compromised passwords immediately; and
- If you’re a business, it’s important to get clear on the legal obligations that you need to comply with such as the Notifiable Data Breach Scheme.
We also encourage you to report scams to the ACCC and spread awareness of Phishing attempts and articles, just like this one, to help keep your friends, your data and your business in safe hands.














